The Domain Name System (DNS) is the cornerstone of communication for the internet. Navigating to the sites you access every day often starts with a DNS request. Cybercriminals recognize the value of DNS and may look for ways to abuse improperly secured DNS to compromise its uptime, integrity or overall response efficacy—which makes DNS an important area for enforcing security and protecting against threats.
One such threat: cache poisoning.
When a DNS request is made, the query is routed to a recursive name server. If the domain name navigation information is cached, the recursive name server sends the response directly back to the user with the appropriate information, so they can go to the intended destination. If the information is not present in the cache, the recursive name server queries other DNS servers to find the information needed to answer the original query.
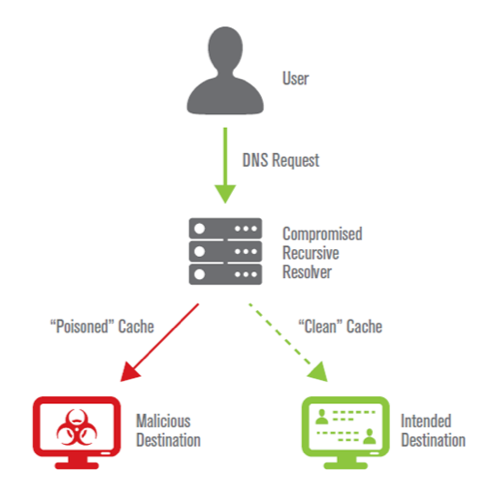
Cybercriminals understand how to manipulate DNS caching and may take advantage of unsecured servers through cache poisoning. Cache poisoning can occur when a cybercriminal sends fake (spoofed) DNS responses to a target recursive name server (resolver), pretending they came from an authoritative name server, a forwarder, or even a recursive name server to a client stub. When malicious information is cached on the recursive name server, the names on the server are considered “poisoned.”
Cybercriminals use cache poisoning to redirect traffic to fraudulent websites and other unintended destinations. Cache poisoning is considered dangerous because it does not require significant bandwidth, processing resources, or technical expertise to execute, and an attacker doesn’t need to be in the data path to launch cache poisoning attacks. Furthermore, a fraudulent address can reside on a recursive name server for hours, days or weeks before it is discovered.
When a poisoned cache connects an unsuspecting user or device to a fraudulent site, cybercriminals can do a variety of things such as, obtain sensitive data and other confidential information, steal user credentials and passwords, eavesdrop on communications, plant malicious software or display images and text that defame a legitimate brand or provide misleading information.
One solution to address cache poisoning is the implementation of DNS security extensions (DNSSEC). DNSSEC is the main security mechanism that protects the integrity of DNS records and helps safeguard the end-to-end integrity and authenticity of DNS responses.
As DNS attacks grow in frequency and impact, organizations can no longer afford to overlook DNS security as part of their overall defense-in-depth strategy. As with IT security in general, no single tactic can address the entire DNS threat landscape or secure the complete DNS ecosystem. The key is to assess risks, identify security gaps and develop a plan to strengthen the security of both your inbound and outbound DNS.
For more information on the importance of DNS in the security ecosystem, and considerations for securing DNS in your organization with DNSSEC and other solutions, please download our free white paper, “Framework for Resilient DNS Security,” here.





Thanks for sharing the blog. It can be helpful to many people to prevent any risk of hacking and protect sensitive data. Security protocols should be the primary focus if you have crucial financial data on the computer because personal communication or images can be breached.